Advanced Encryption in Cloud Computing Environments
In an era dominated by the ever-expanding realm of cloud computing, the seamless flow of information and the rapid exchange of data have become integral components of modern business operations. However, this digitized landscape also brings forth an array of security concerns, highlighting the critical need for robust protective measures. At the forefront of this cyber-defense arsenal lies encryption, a technology that transforms sensitive data into an unreadable format, shielding it from unauthorized access. While encryption has long been a staple in information security, the dynamic nature of cloud environments necessitates the exploration and implementation of advanced encryption techniques tailored to address the unique challenges posed by shared resources, data transmission vulnerabilities, and the omnipresent specter of insider threats.
Encryption Challenges in Cloud Computing
The adoption of cloud computing brings forth a myriad of benefits, yet it is not without its security challenges. One prominent hurdle is the shared resources and multi-tenancy model inherent in cloud environments. While the concept of shared infrastructure allows for cost efficiency and resource optimization, it introduces potential vulnerabilities. In a multi-tenant setup, multiple users share the same hardware, creating a scenario where data isolation becomes crucial. Advanced encryption measures must be in place to ensure that data from different tenants remains confidential and inaccessible to unauthorized parties.

Data transmission vulnerabilities represent another critical concern. As data traverses the vast and interconnected networks of the cloud, it becomes susceptible to interception and unauthorized access. Encryption plays a pivotal role in securing data in transit, safeguarding it from potential eavesdropping and man-in-the-middle attacks. Robust encryption protocols, such as Transport Layer Security (TLS), are essential to fortify the integrity of data as it moves between users and the cloud servers.
Additionally, the specter of insider threats looms large in cloud computing. Despite stringent access controls, the very nature of cloud systems, where multiple entities share the same infrastructure, increases the risk of insider malfeasance. Advanced encryption not only protects against external threats but also serves as a crucial defense against unauthorized access from within the organization.
Furthermore, compliance and regulatory issues pose a substantial challenge in cloud environments. Different regions and industries have varying data protection requirements, and organizations must navigate a complex landscape of regulations. Encryption becomes a linchpin in achieving compliance, ensuring that data is handled and stored in accordance with relevant laws and standards. Addressing these challenges head-on is imperative for organizations looking to harness the full potential of cloud computing while maintaining the highest standards of data security and regulatory compliance.
Key Management in Cloud Environments
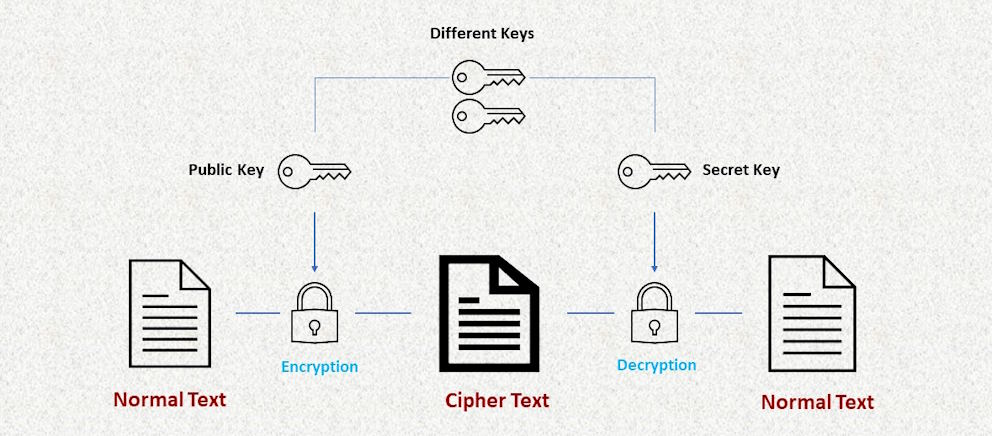
While encryption stands as a stalwart defender of data integrity in cloud computing, effective key management emerges as the unsung hero in this dynamic security landscape. Key management, however, is not without its challenges. The sheer scale and complexity of cloud environments often lead to difficulties in securely generating, storing, and distributing cryptographic keys. The need for a centralized and efficient key management strategy becomes evident as organizations grapple with the intricacies of securing data across diverse cloud infrastructures.
Enter Hardware Security Modules (HSMs). These dedicated hardware devices provide a robust solution to the challenges of key management in the cloud. By safeguarding cryptographic keys in tamper-resistant hardware, HSMs bolster the overall security posture. Cloud providers increasingly offer HSM services, allowing organizations to benefit from specialized hardware without the burden of physical maintenance. The integration of HSMs in cloud environments adds an extra layer of protection, ensuring that cryptographic keys remain secure and accessible only to authorized entities.
Key rotation and lifecycle management are integral components of a comprehensive key management strategy. Regularly updating cryptographic keys and managing their lifecycle effectively guards against potential vulnerabilities. Automation plays a crucial role in this process, facilitating the seamless rotation of keys without disrupting operations. A well-executed key management strategy, encompassing both HSMs and meticulous lifecycle management, is pivotal in ensuring that the keys to the kingdom remain firmly in the hands of those who are entrusted with securing the cloud infrastructure.


